[C2C CTF 2023] Hemp & Brave
Description
These images have been passing through
suspicious Twitter activity. Can you find out
anything useful from them?
Solution
This really took a while. No forensic tools give you anything useful, and it’s really hard to find anomalies in the image by inspection.
But you can use tineye to try to find the original photo online. If you sort by image size, you find that the largest one is the same size.
Use the Python Pillow library to compare them pixel by pixel:
from PIL import Image
import numpy as np
import itertools
im = Image.open('CanberraFile.png')
o = Image.open('original.png')
im1 = im.convert("RGB")
im2 = o.convert("RGB")
np1 = np.array(im1)
np2 = np.array(im2)
# The first 10 pixels are different:
for x,y,z in itertools.product(range(2000), range(4000), range(3)):
if not (np1[x,y,z] == np2[x,y,z]):
print(x,y,z)
You get the output that lists the first 11 pixels as all different, and you can verify that by looking at the image again:
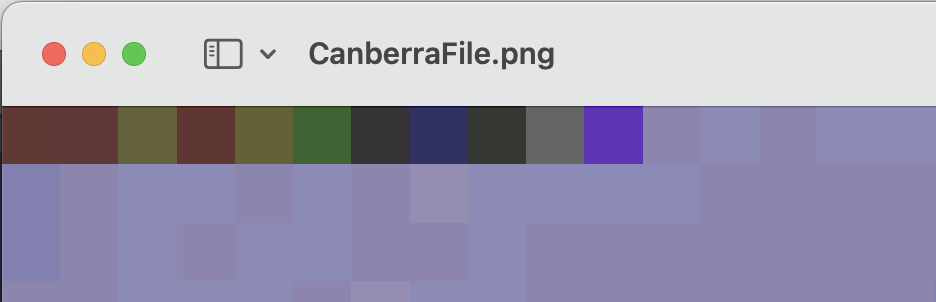
Once you have that, you can extract them, and try to decode them as ASCII:
s = "".join([chr(c) for c in np1[0,0:11].flatten()])
print(s)
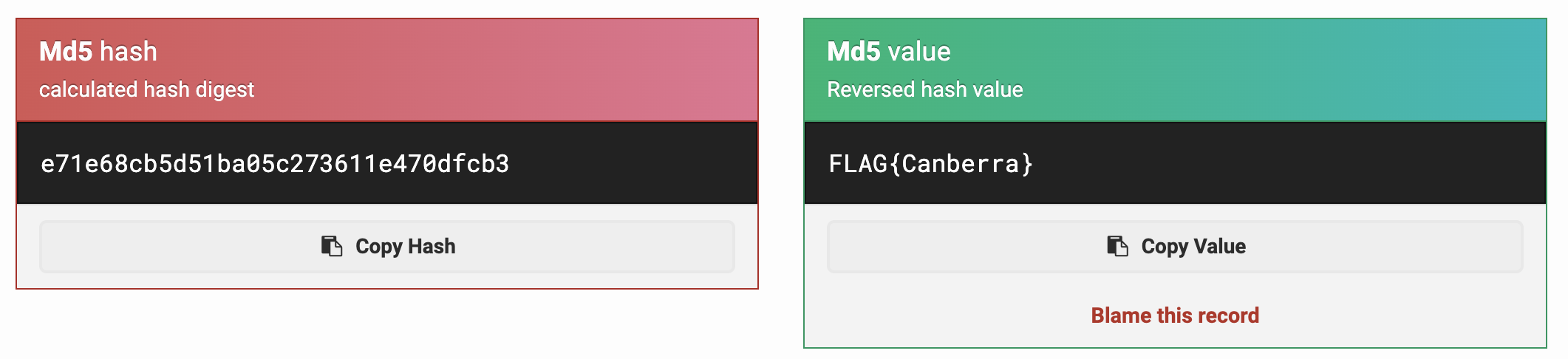
# Output: e71e68cb5d51ba05c273611e470dfcb3¹
The last character is a superscript 1, but, as you had 11 pixels with 3 colours each, that means that you have exactly 32 bytes of ASCII. This hash is not in a wordlist so is more difficult to crack. I originally got the answer by using a website called md5hashing.net, but I’m a bit suspicious about the source of that hash one the site.
Through the power of hindsight and knowing the flag, I found another way of doing this. You can reasonably expect that the input to the hashing function will have the format FLAG{...}. You can create a rule for hashcat to try this on the wordlist:
$ cat rule
^{^G^A^L^F$}
$ hashcat -m 0 -r rule e71e68cb5d51ba05c273611e470dfcb3 rockyou.txt
...
e71e68cb5d51ba05c273611e470dfcb3:FLAG{Canberra}
...
Flag
FLAG{Canberra}
